Ultimate Guide to What a Replay Attack is
Table of Interests
Looking for the best article to study about replay attack?, then Ultimate Guide to What a Replay Attack is is for you.
A replay attack, sometimes also called a playback attack, is a cyber attack in which the malicious entity intercepts and then repeats a valid data transmission going through a network. Owing to the validity of the original data (which typically comes from an authorized user) the network’s security protocols treat the attack as if it were a normal data transmission. Since the original messages are intercepted and re-transmitted verbatim, hackers employing replay attacks do not necessarily need to decrypt them.
What Can Hackers Do With a Replay Attack?
Replay attacks can be used to gain access to information stored on an otherwise protected network by passing it seemingly valid credentials. They can also be used to fool financial institutions into duplicating transactions, allowing attackers to draw money directly out of their victims’ accounts. In some cases, hackers will combine parts of different encrypted messages and pass the resulting ciphertext to the network in what is known as a cut-and-paste attack. The network’s reaction to this kind of attack will often give the hacker valuable information that can be used to further exploit the system.
Despite the obvious dangers associated with them, there are limits to what hackers can achieve with replay attacks alone. Attackers cannot change the data that is being sent without the network rejecting it, limiting the effectiveness of the attack to repeating past actions. These attacks are also relatively easy to defend against. A defense as basic as adding a timestamp to data transmission can guard against simple replay attempts. Servers can also cache repeated messages and cut them off after a certain number of repetitions to limit the number of attempts an attacker can make by replaying messages in quick succession.
Why Replay Attacks Matter in the World of Cryptocurrencies
Though they are far from exclusive to it, these attacks are particularly relevant to the environment of cryptocurrency transactions and blockchain ledgers. The reason for this is that blockchain ledgers sometimes go through protocol changes or upgrades known as hard forks. When a hard fork takes place, the existing ledger splits into two, with one running the legacy version of the software and one running the new, updated version. Some hard forks are meant merely to upgrade the ledger, while others branch off and effectively form entirely new cryptocurrencies. One of the best-known examples of a hard fork of the latter variety is the one that allowed Bitcoin Cash to fork from the main Bitcoin blockchain on August 1st, 2017.
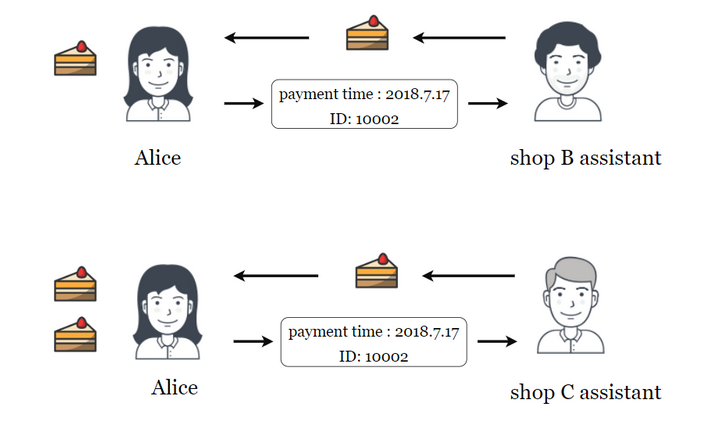
When these hard forks occur, it becomes theoretically possible for attackers to employ replay attacks against blockchain ledgers. A transaction processed on one ledger by a person whose wallet was valid before the hard fork will also be valid on the other one. As a result, a person who received a certain number of cryptocurrency units from someone else through one ledger could switch to the other ledger, replicate the transaction and fraudulently transfer an identical number of units to his or her account a second time. Because their wallets are not part of the shared history of the ledgers, users who come to a blockchain after a hard fork takes place are not vulnerable to these attacks.
How Can Blockchains Be Protected Against These Attacks?
Although the vulnerability of forked blockchain ledgers to replay attacks is a valid concern, most hard forks include security protocols that are specifically designed to prevent these attacks from being successful. Effective measures against blockchain replay attacks fall into two categories, known as strong replay protection and opt-in replay protection. In strong replay protection, a special marker is added to the new ledger that emerges from the hard fork to ensure that the transactions conducted on it will not be valid on the legacy ledger, as well as the other way around. This is the type of protection that was implemented when Bitcoin Cash forked from Bitcoin.
When implemented, the strong replay protection is executed automatically as soon as the hard fork occurs. However, opt-in replay protection requires users to manually make changes to their transactions to ensure these cannot be replayed. Opt-in protection can be useful in instances where the hard fork is intended as an upgrade of a cryptocurrency’s main ledger, rather than as a complete split from it.
In addition to these ledger-wide solutions, individual users can also take steps to protect themselves from being the victims of replay attacks. One method for doing this is by locking coins from being transferred until the ledger reaches a certain number of blocks, thus preventing any replay attack involving those coin units from being verified by the network. It should be noted, though, that not all wallets or ledgers offer this function.
Closing Thoughts
Replay attacks represent a real threat to network security when they are successful. Unlike many other types of attacks, replay attacks do not rely on the decryption of data, making them an effective workaround for malicious actors who are increasingly confronted with secure encryption protocols. Because of the hard forks that are used to upgrade or split them, blockchain ledgers are especially vulnerable to this kind of cyber attack. However, robust solutions exist that are reasonably effective in protecting blockchain systems from them. In particular, the employment of strong replay protection can guarantee that attackers will be unable to replicate transactions after a hard fork takes place
That’s the much we can take on the topic “Ultimate Guide to What a Replay Attack is “.
Thanks For Reading
O3SCHOOLS TEAM
Common Cryptocurrency Scams on Mobile Devices
Ultimate Guide to Symmetric versus Asymmetric Encryption
How Blockchain Is Used in The Internet of Things (IoT)
Ultimate Guide to Understanding What Makes a Blockchain Secure
Upto Date Blockchain Use Cases
Initial Coin Offering List – Comprehensive List of Projects Currently Doing ICO
Ultimate Guide to Initial Coin Offering (ICO)
Ultimate Guide to Understanding What Fractional Reserve is
Understanding Why Public WiFi Is Insecure
The Ultimate History of Cryptography
Understanding what DoS Attack is
Ultimate Guide to what Fiat Currency is
Ultimate Guide to zk-SNARKs and zk-STARKs
Things to Avoid When Using Binance Chain
How Blockchain Is Used In Charity
How Blockchain is Used in Supply Chain
Ultimate Guide to What a Replay Attack is
Ultimate Guide to Delegated Proof of Stake
Ultimate Guide to what Ransomware is
Ultimate Guide to understanding Cryptojacking
Ultimate Guide to Understanding Inflation for Beginners
How to Know Cryptocurrencies Pyramid and Ponzi Schemes
Ultimate Beginner’s Guide to Bitcoin’s Lightning Network
Advantages and Disadvantages Of Blockchain
Ultimate Guide to Ethereum Plasma
Leave a Reply