Ultimate Guide to Understanding Public Key Cryptography
Table of Interests
Looking for the best content to study on Public Key Cryptography, then Ultimate Guide to Understanding Public Key Cryptography is for you.
Public key cryptography (PKC), also known as asymmetric cryptography, is a framework that uses both a private and a public key, as opposed to the single key used in symmetric cryptography. The use of key pairs gives PKC a unique set of characteristics and capabilities that can be utilized to solve challenges inherent in other cryptographic techniques. This form of cryptography has become an important element of modern computer security, as well as a critical component of the growing cryptocurrency ecosystem.
How does public key cryptography work?
In a PKC scheme, the public key is used by a sender to encrypt information, while the private key is used by a recipient to decrypt it. Because the two keys are different from one another, the public key can be safely shared without compromising the security of the private one. Each asymmetric key pair is unique, ensuring that a message encrypted using a public key can only be read by the person who possesses the corresponding private key.
Because asymmetric encryption algorithms generate key pairs that are mathematically linked, their key lengths are much longer than those used in symmetric cryptography. This longer length – typically between 1,024 and 2,048 bits – makes it extremely difficult to compute a private key from its public counterpart. One of the most commons algorithm for asymmetric encryption in use today is known as RSA.
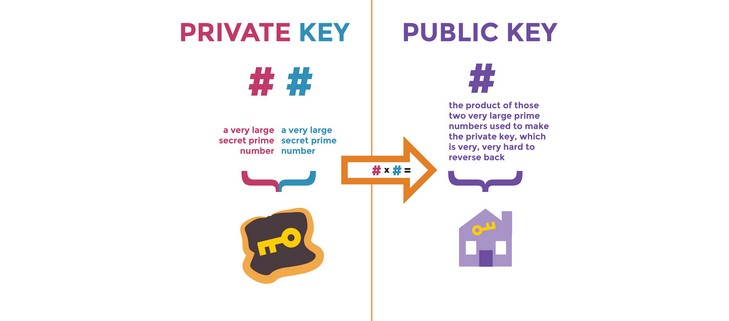
In the RSA scheme, keys are generated using a modulus that is arrived at by multiplying two numbers (often two large prime numbers). In basic terms, the modulus generates two keys (one public that can be shared, and one private that should be kept in secret). The RSA algorithm was first described in 1977 by Rivest, Shamir, and Adleman (hence, RSA) and remains a major component of public key cryptography systems.
PKC as an encryption tool
Public key cryptography solves one of the long-standing problems of symmetric algorithms, which is the communication of the key that is used for both encryption and decryption. Sending this key over an insecure connection risks exposing it to third parties, who can then read any messages encrypted with the shared key. Although cryptographic techniques (such as the Diffie-Hellman-Merkle key exchange protocol) exist to solve this problem, they are still vulnerable to attacks. In public key cryptography, by contrast, the key used for encryption can be shared securely over any connection. As a result, asymmetric algorithms offer a higher level of protection when compared to the symmetric ones.
Generating digital signatures
Another application of asymmetric cryptography algorithms is that of authenticating data through the use of digital signatures. Basically speaking, a digital signature is a hash created using the data in a message. When that message is sent, the signature can be checked by the recipient using the sender’s public key. This way, they can authenticate the source of the message and ensure that it has not been tampered with. In some cases, digital signatures and encryption are applied together, meaning the hash itself may be encrypted as part of the message. It should be noted, however, that not all digital signature schemes use encryption techniques.
Limitations
Although it can be used to enhance computer security and provide verification of message integrity, PKC does have some limitations. Owing to the complex mathematical operations involved in encryption and decryption, asymmetric algorithms can be quite slow when forced to deal with large amounts of data. This type of cryptography also depends heavily on the assumption that the private key will remain secret. If a private key is accidentally shared or exposed, the security of all messages that have been encrypted with its corresponding public key will be compromised. It is also possible for users to accidentally lose their private keys, in which case it becomes impossible for them to access the encrypted data.
Applications of public key cryptography
This type of cryptography is used by many modern computer systems to provide security for sensitive information. Emails, for example, can be encrypted using public key cryptography techniques to keep their contents confidential.
The secure sockets layer (SSL) protocol that makes secure connections to websites possible also employs asymmetric cryptography. PKC systems have even been explored as a means of providing a secure electronic voting environment that would potentially allow voters to participate in elections from their home computers.
PKC also features prominently in blockchain and cryptocurrency technology. When a new cryptocurrency wallet is set up, a pair of keys is generated (public and private keys). The wallet address is generated using the public key and can be securely shared with others. The private key, on the other hand, is used for creating digital signatures and verifying transactions, and therefore, must be kept in secret.
Once a transaction has been verified by confirming the hash contained in the digital signature, that transaction can be added to the blockchain ledger. This system of digital signature verification ensures that only the person who has the private key associated with the corresponding cryptocurrency wallet can move the funds.
It should be noted that the asymmetric cryptography used in cryptocurrency applications are different from those used for computer security purposes. Bitcoin and Ethereum, for instance, use a specific algorithm to verify transactions, known as the Elliptic Curve Digital Signature Algorithm (ECDSA). Also, the ECDSA creates digital signatures without the use of encryption. This means that blockchain doesn’t need encryption, unlike many tend to believe.
Closing thoughts
From computer security to verifying cryptocurrency transactions, public key cryptography plays an important role in securing modern digital systems. By using paired public and private keys, asymmetric cryptography algorithms resolve fundamental security concerns presented by symmetric ciphers. Although PKC has been in use for many years, new uses and applications are regularly being developed for it, particularly in the blockchain and cryptocurrency space.
That’s the much we can take on the topic “Ultimate Guide to Understanding Public Key Cryptography “.
Thanks For Reading
O3SCHOOLS TEAM
Common Cryptocurrency Scams on Mobile Devices
Ultimate Guide to Symmetric versus Asymmetric Encryption
How Blockchain Is Used in The Internet of Things (IoT)
Ultimate Guide to Understanding What Makes a Blockchain Secure
Upto Date Blockchain Use Cases
Initial Coin Offering List – Comprehensive List of Projects Currently Doing ICO
Ultimate Guide to Initial Coin Offering (ICO)
Ultimate Guide to Understanding What Fractional Reserve is
Understanding Why Public WiFi Is Insecure
The Ultimate History of Cryptography
Understanding what DoS Attack is
Ultimate Guide to what Fiat Currency is
Ultimate Guide to zk-SNARKs and zk-STARKs
Things to Avoid When Using Binance Chain
How Blockchain Is Used In Charity
How Blockchain is Used in Supply Chain
Ultimate Guide to What a Replay Attack is
Ultimate Guide to Delegated Proof of Stake
Ultimate Guide to what Ransomware is
Ultimate Guide to understanding Cryptojacking
Ultimate Guide to Understanding Inflation for Beginners
How to Know Cryptocurrencies Pyramid and Ponzi Schemes
Ultimate Beginner’s Guide to Bitcoin’s Lightning Network
Advantages and Disadvantages Of Blockchain
Ultimate Guide to Ethereum Plasma
Leave a Reply