Ultimate Guide to Pretty Good Privacy PGP
Table of Interests
Looking for the best article to read on Pretty Good Value?, then “Ultimate Guide to Pretty Good Privacy PGP” is for you.
PGP stands for Pretty Good Privacy. It is an encryption software designed to provide privacy, security, and authentication for online communication systems. Phil Zimmerman is the name behind the first PGP program, and according to him, it was made freely available due to the growing social demand for privacy.
Since its creation in 1991, many versions of PGP software were created. In 1997, Phil Zimmerman made a proposal to the Internet Engineering Task Force (IETF) for the creation of an open-source PGP standard. The proposal was accepted and led to the creation of the OpenPGP protocol, which defines standards formats for encryption keys and messages.
Although initially used only for securing email messages and attachments, PGP is now applied to a wide range of use cases, including digital signatures, full disk encryption, and network protection.
PGP was initially owned by the company PGP Inc, which was later acquired by Network Associates Inc. In 2010, Symantec Corp. acquired PGP for $300 million, and the term is now a trademark used for their OpenPGP-compliant products.
How does it work?
PGP is among the first widely available software to implement public key cryptography. It is a hybrid cryptosystem that uses both symmetric and asymmetric encryption to achieve a high level of security.
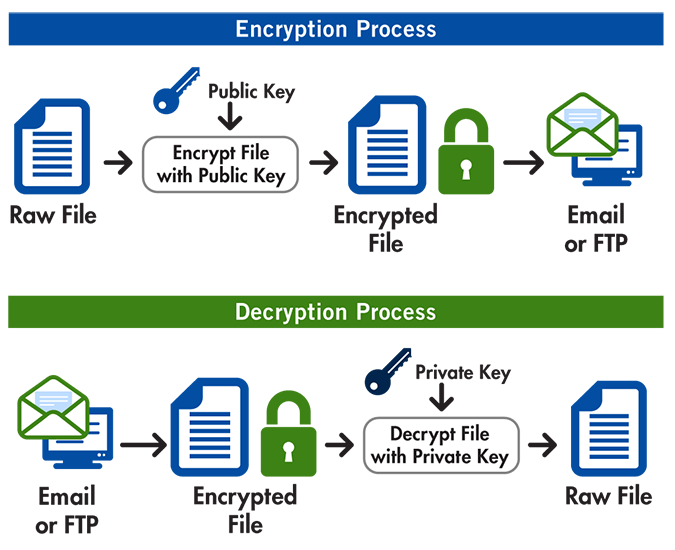
In a basic process of text encryption, a plaintext (data that can be clearly understood) is converted into ciphertext (unreadable data). But before the process of encryption takes place, most PGP systems perform data compression. By compressing plaintext files prior to transmitting them, PGP saves both disk space and transmission time – while also improving security.
Following the file compression, the actual process of encryption begins. At this stage, the compressed plaintext file is encrypted with a single-use key, which is known as the session key. This key is randomly generated through the use of symmetric cryptography, and each PGP communication session has a unique session key.
Next, the session key (1) itself is encrypted using asymmetric encryption: the intended receiver (Bob) provides his public key (2) to the sender of the message (Alice) so that she can encrypt the session key. This step allows Alice to safely share the session key with Bob through the Internet, regardless of security conditions.
The asymmetric encryption of the session key is usually done through the use of the RSA algorithm. Many other encryption systems use RSA, including the Transport Layer Security (TLS) protocol that secures a great portion of the Internet.
Once the message’s ciphertext and the encrypted session key are transmitted, Bob can use his private key (3) to decrypt the session key, which is then used to decrypt the ciphertext back into the original plaintext.
Aside from the basic process of encryption and decryption, PGP also supports digital signatures – which serve at least three functions:
Authentication: Bob can verify that the sender of the message was Alice.
Integrity: Bob can be sure that the message wasn’t altered.
Non-repudiation: after the message is digitally signed, Alice cannot claim she didn’t send it.
Use cases
One of the most common uses for PGP is to secure emails. An email that is protected with PGP is turned into a string of characters that are unreadable (ciphertext) and can only be deciphered with the corresponding decryption key. The working mechanisms are practically the same for securing text messages, and there are also some software applications that allow PGP to be implemented on top of other Apps, effectively adding an encryption system to non-secured messaging services.
Although PGP is mostly used to secure internet communications, it can also be applied to encrypt individual devices. In this context, PGP may be applied to disk partitions of a computer or mobile device. By encrypting the hard disk, the user will be required to provide a password every time the system boots up.
Advantages and disadvantages
Thanks to its combined use of symmetric and asymmetric encryption, PGP allows users to securely share information and cryptographic keys through the Internet. As a hybrid system, PGP benefits from both the security of asymmetric cryptography and the speed of symmetric encryption. In addition to security and speed, digital signatures ensure the integrity of the data and authenticity of the sender.
The OpenPGP protocol allowed for the emergence of a standardized competitive environment and PGP solutions are now provided by multiple companies and organizations. Still, all PGP programs that comply with the OpenPGP standards are compatible with each other. This means that files and keys generated in one program may be used in another without problems.
Regarding the disadvantages, PGP systems are not that simple to use and understand, especially for users with little technical knowledge. Also, the long length of the public keys is deemed by many as quite inconvenient.
In 2018, a major vulnerability called EFAIL was published by the Electronic Frontier Foundation (EFF). EFAIL made it possible for attackers to exploit active HTML content in encrypted emails to gain access to the plaintext versions of messages.
However, some of the concerns described by EFAIL were already known by the PGP community since the late 1990s and, in fact, the vulnerabilities are related to the different implementations on the part of email clients, and not with PGP itself. So despite the alarming and misleading headlines, PGP is not broken and continues to be highly secure.
Closing thoughts
Since its development in 1991, PGP has been an essential tool for data protection and is now used in a wide range of applications, providing privacy, security, and authentication for several communication systems and digital service providers.
While the 2018 discovery of the EFAIL flaw raised significant concerns about the protocol’s viability, the core technology is still regarded as robust and cryptographically sound. It is worth noting that different PGP implementations may present varying levels of security.
That’s the much we can take on the topic “Ultimate Guide to Pretty Good Privacy PGP“.
Thanks For Reading
Common Cryptocurrency Scams on Mobile Devices
Ultimate Guide to Symmetric versus Asymmetric Encryption
How Blockchain Is Used in The Internet of Things (IoT)
Ultimate Guide to Understanding What Makes a Blockchain Secure
Upto Date Blockchain Use Cases
Initial Coin Offering List – Comprehensive List of Projects Currently Doing ICO
Ultimate Guide to Initial Coin Offering (ICO)
Ultimate Guide to Understanding What Fractional Reserve is
Understanding Why Public WiFi Is Insecure
The Ultimate History of Cryptography
Understanding what DoS Attack is
Ultimate Guide to what Fiat Currency is
Ultimate Guide to zk-SNARKs and zk-STARKs
Things to Avoid When Using Binance Chain
How Blockchain Is Used In Charity
How Blockchain is Used in Supply Chain
Ultimate Guide to What a Replay Attack is
Ultimate Guide to Delegated Proof of Stake
Ultimate Guide to what Ransomware is
Ultimate Guide to understanding Cryptojacking
Ultimate Guide to Understanding Inflation for Beginners
How to Know Cryptocurrencies Pyramid and Ponzi Schemes
Ultimate Beginner’s Guide to Bitcoin’s Lightning Network
Advantages and Disadvantages Of Blockchain
Ultimate Guide to Ethereum Plasma
Leave a Reply