How Exposed You Are Using Device Fingerprinting
Table of Interests
Looking for Best article on Device Fingerprinting, then “How Exposed You Are Using Device Fingerprinting”, is for you.
In computer science, fingerprinting refers to the process of creating unique identifiers – for all sorts of digital data. But when certain techniques are deployed to identify individual users or machines, we refer to them as browser or device fingerprinting.
Essentially, the process consists of gathering information about a smartphone, computer, or other devices. Sometimes, this can be achieved even when the user’s IP address is hidden or when they change from one browser to another.
For many years, web analytics services have been collecting devices and browser information, aiming to measure legitimate web traffic and detect potential frauds. Today, more advanced approaches allow for the collection of specific parameters.
Previous fingerprinting methods focused mainly on computers. But, modern techniques can now identify devices of almost any type, and there is an increasing interest in the growing mobile environment.
How does it work?
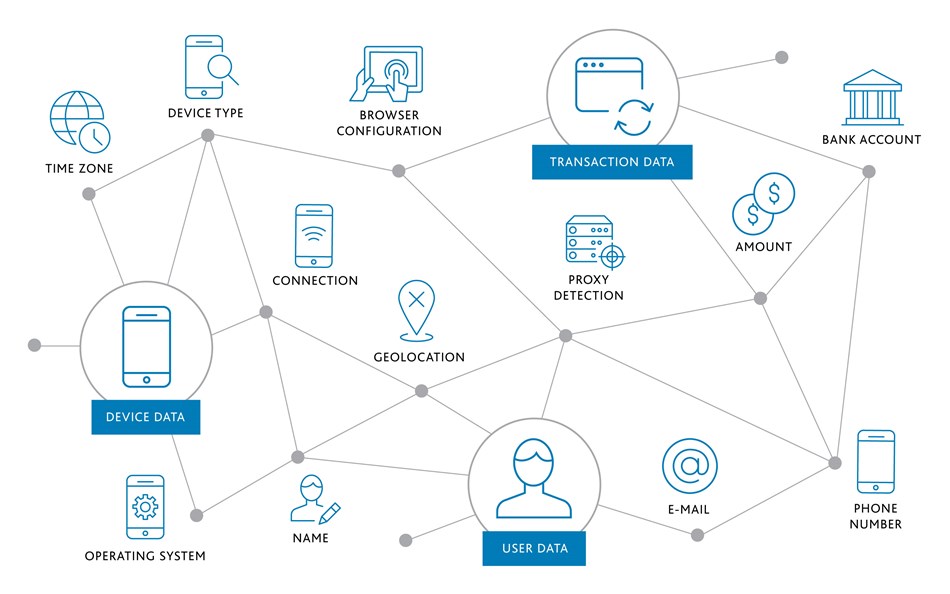
Specifically, device fingerprinting involves the collection of data sets, which are then combined and submitted through a hash function. Next, the output (hash value) may serve as a unique ID for each device (or user).
The information gathered is often stored in a database, rather than on the device itself. While a single data point is somewhat generic, the combination of multiple data sets can be unique.
Device fingerprinting may include both passive and active methods. The goal of both approaches is to collect a device’s information. So even if thousands of computers are running the same operating system, each will likely present a unique combination of software, hardware, browser, plugins, language, time zone, and general settings.
Passive fingerprinting
As the name suggests, passive methods gather information in a less obvious way, without querying the user (or the remote system). The data is collected based on what is sent out by each device, so passive fingerprinting tends to provide less specific information (e.g., operating system).
For instance, one can develop a passive fingerprinting technique that collects information about a wireless driver on networking devices, such as an Internet modem. The passive interaction could be explored in various types of drivers, without requiring any action from the devices. Simply put, different devices adopt different methods for scanning possible connections (access points). So, these differences can be used by an attacker to accurately identify which driver is being used by each targeted device.
Active fingerprinting
On the other hand, active fingerprinting relies on active network communication, which makes them more detectable on the client-side. Some websites run JavaScript code as a way to gather information about the user’s devices and browsers. This may include window size, fonts, plugins, language settings, time zone, and even details about their hardware.
A notable example of an active technique is canvas fingerprinting, which is used on both computer and mobile devices. It often relies on a script that interacts with the canvas (graphics element) of an HTML5 web page. The script instructs the canvas to draw a hidden image on the screen and then records the information represented in the image, such as screen resolution, fonts, and background colors.
What is it used for?
Device fingerprinting methods provide a way for advertisers to track consumer behavior across multiple browsers. They also allow banks to identify if a request is coming from a trusted device or from a system associated that was previously associated with fraudulent activity.
Other than that, device fingerprinting help websites prevent multiple account registrations or a search engine to flag devices demonstrating suspicious behavior.
Device fingerprints may come handy when detecting and preventing identity theft or credit card fraud. However, these techniques threaten user privacy and depending on the implementation, the collection of data can be undetectable – especially with passive fingerprinting.
What are the limitations?
When it comes to active fingerprinting, the data collection relies on the availability of scripting languages, such as JavaScript. Mobile devices and users that run privacy software or plugins will likely present limited scripting availability, making them harder to identify. This includes the use of browser extensions that block trackers and ads.
In some situations, however, privacy-focused users can be easier to identify. For instance, when they use unpopular software and plugins along with particular settings that, ironically, make them even more distinctive.
Also, the effectiveness of fingerprinting may be limited by large variations on the client-side. Users that are constantly changing their settings, or that use multiple virtual operating systems may cause inaccuracies in the process of data collection.
Using different browsers may as well cause inconsistencies in the process of gathering information, but modern, cross-browser fingerprinting techniques can be used to avoid such limitation.
Closing thoughts
There are several ways of implementing and using the device fingerprinting technique. So, the effectiveness to gather data and identify a single source may vary considerably from one method to another.
Either on its own or when combined with other methods, device fingerprinting can be an effective tool for tracking behavior and identifying users. As such, this powerful technique can be used for both legit and shady activities, so being informed about their basic mechanisms is certainly a good starting point.
That’s the much we can take on the topic “How Exposed You Are Using Device Fingerprinting“.
Thanks For Reading
Common Cryptocurrency Scams on Mobile Devices
Ultimate Guide to Symmetric versus Asymmetric Encryption
How Blockchain Is Used in The Internet of Things (IoT)
Ultimate Guide to Understanding What Makes a Blockchain Secure
Upto Date Blockchain Use Cases
Initial Coin Offering List – Comprehensive List of Projects Currently Doing ICO
Ultimate Guide to Initial Coin Offering (ICO)
Ultimate Guide to Understanding What Fractional Reserve is
Understanding Why Public WiFi Is Insecure
The Ultimate History of Cryptography
Understanding what DoS Attack is
Ultimate Guide to what Fiat Currency is
Ultimate Guide to zk-SNARKs and zk-STARKs
Things to Avoid When Using Binance Chain
How Blockchain Is Used In Charity
How Blockchain is Used in Supply Chain
Ultimate Guide to What a Replay Attack is
Ultimate Guide to Delegated Proof of Stake
Ultimate Guide to what Ransomware is
Ultimate Guide to understanding Cryptojacking
Ultimate Guide to Understanding Inflation for Beginners
How to Know Cryptocurrencies Pyramid and Ponzi Schemes
Ultimate Beginner’s Guide to Bitcoin’s Lightning Network
Advantages and Disadvantages Of Blockchain
Ultimate Guide to Ethereum Plasma
Leave a Reply